Unified SSO for Azure Active Directory
Data hub rollout
Engagement customers are being upgraded to unified login in several phases. Your registered support contacts will be notified when the login experience is upgraded for your organization. If your account hasn't been upgraded yet, the pre-existing Administration documentation still applies.
Single sign-on (SSO) authentication for Azure Active Directory (Azure AD) lets your team access Bloomreach using their existing company credentials.
This guide walks you through configuring Azure AD as your identity provider using SAML 2.0 authentication.
Prerequisites
Before configuring SSO in Azure AD, ensure you have:
- Admin role in Bloomreach
- Admin access to Azure AD identity provider
- Active SSO feature on your Bloomreach account (contact your Customer Success Manager for activation)
Configure Azure AD SSO
To use Azure AD SSO login, you must first configure it in your Azure AD dashboard.
Info
You'll switch between Azure AD and Bloomreach multiple times during this configuration. Keep both dashboards open to streamline the process
- Azure AD: Create and set up the enterprise application (Step 1-3).
- Bloomreach: Download service provider metadata (Step 4).
- Azure AD: Upload metadata, configure claims, and get metadata URL (Step 5-7).
- Bloomreach: Complete the configuration (Step 8).
Step 1: Create an enterprise application
Go to your Azure AD dashboard and access enterprise applications:
- Go to Manage > Enterprise Applications from the left menu.
- Click + New application.
- Select + Create your own application.
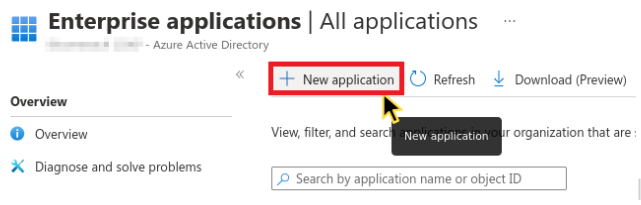
Creating new application in Azure AD Enterprise Applications page.
Step 2: Set up the application
In the modal window, configure your new application:
- Enter a name (for example, "Bloomreach").
- Select Integrate any other application you don't find in the gallery (Non-gallery).
- Click Create.
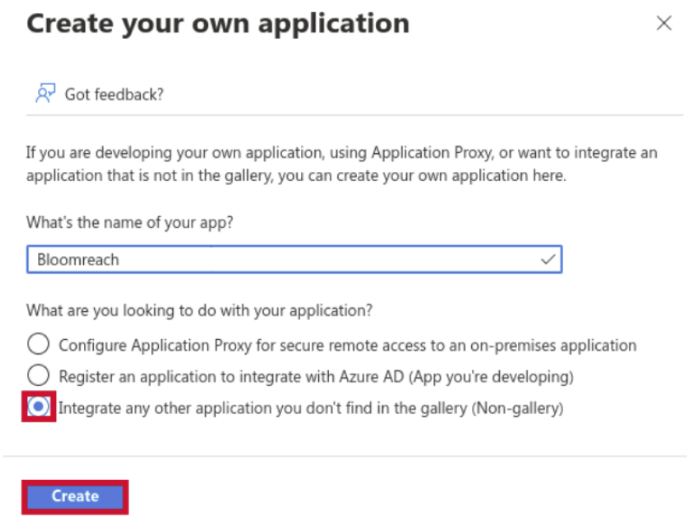
Create application with the application name.
Step 3: Select SAML authentication
Configure SSO for the application:
- From the left Manage menu, select Single sign-on.
- Choose SAML from the available sign-on methods.
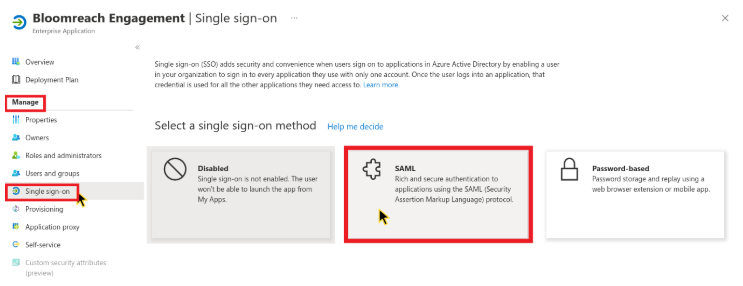
Choose SAML in single sign-on optoins.
Step 4: Enable SSO and download service provider metadata
Switch to Bloomreach to enable SSO and download service provider metadata:
- Go to Administration > Settings > Single sign-on > Preferences.
- Enable the Single sign-on integration toggle.
- Click Download service provider metadata.
- Save the file as
service-provider-metadata.xml
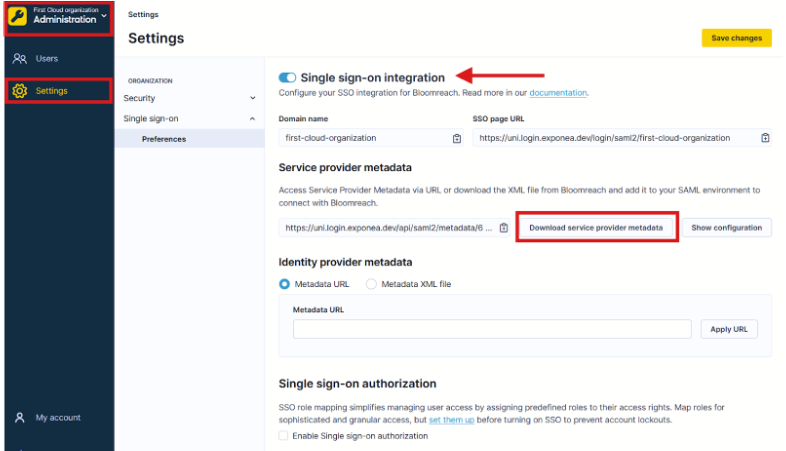
Enable SSO and download service provider metadata from Bloomreach settings.
Step 5: Upload metadata
Return to Azure AD and:
- Click Upload metadata file.
- Select the XML file you downloaded from Bloomreach Administration section.
- Review the Basic SAML Configuration extracted from the metadata.
- Click Save.
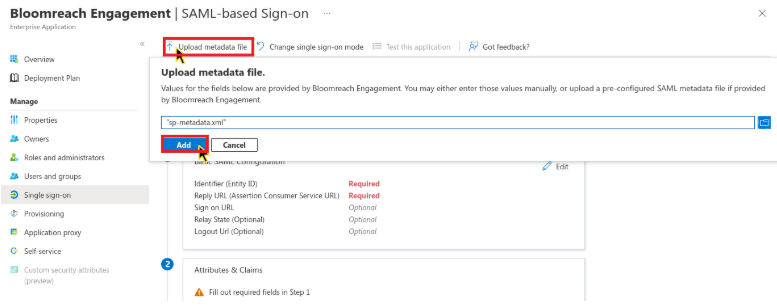
Upload metadata to Azure AD.
Step 6: Configure attributes and claims
Set up the required user attributes for authentication:
- Go to the Attributes & Claims section.
- Click Edit.
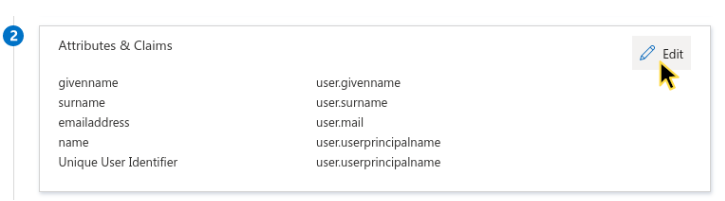
Attributes and claims in Azure AD.
- Remove all Additional claims (keep the Required claim unchanged).
- Add three new claims using + Add new claim. Claims are listed in the table below.
Configure mandatory claims and verify that they match the values exactly:
| Claim name | Source | Source attribute |
|---|---|---|
email | Attribute | user.userprincipalname |
first_name | Attribute | user.givenname |
last_name | Attribute | user.surname |
Configure optional claims:
- Mobile phone claim (
user.mobilephone) if you have mobile phone data available. - Email address claim (
user.email)and unique name ID claim if users can't receive emails to the email addresses defined in theuser.userprincipalnamefield.
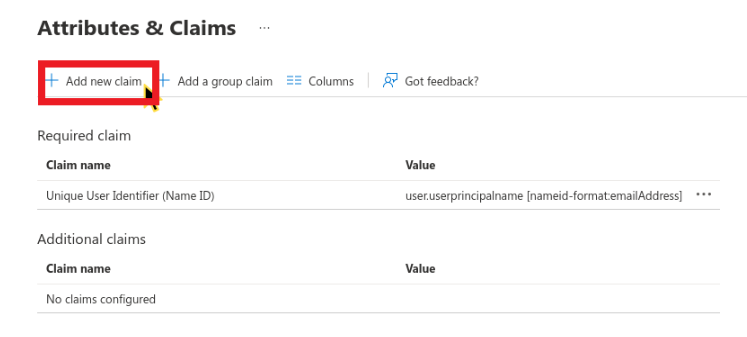
Add a new claim to Azure AD.
Step 7: Get metadata URL
Get the metadata URL from Azure AD:
- Go to SAML Signing Certificate.
- Copy the App Federation Metadata URL to your clipboard. You'll need it in the next step.
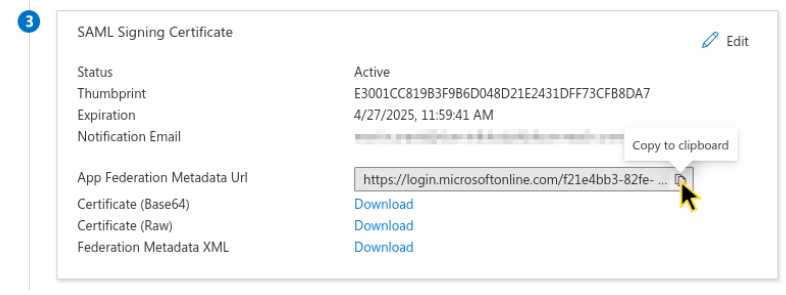
Copy the App federation metadata URL to the clipboard.
Step 8: Complete the configuration
Finish the configuration in Bloomreach:
- Go to Administration > Settings > Preferences.
- Paste the URL into the Metadata URL field under Identity provider metadata.
- Click Apply URL. Verify that the metadata contains a valid single sign-on URL and that the encryption/signing certificates haven't expired.
- Click Save changes.
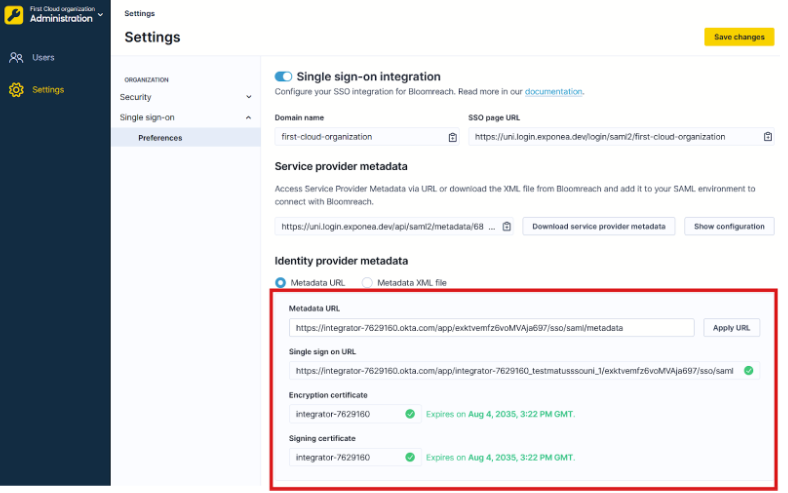
Paste the metadata URL to Bloomreach.
- Go to Administration > Settings > Security > Authentication settings.
- Enable single sign-on as an allowed authentication method.
- Optionally disable other authentication methods to enforce SSO.
- Click Save changes.
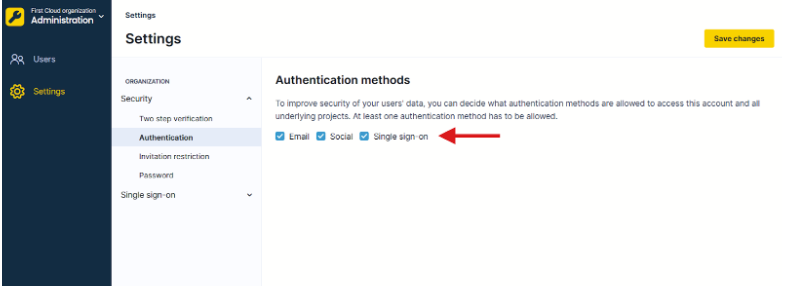
Enable SSO in Bloomreach.
All users you assign to the application in Azure AD can now log in to the Bloomreach application and access their subscribed Bloomreach products using Azure AD SSO.
Next steps
- Assign users to the application in Azure AD.
- Assign user roles via SSO (see Unified SSO authorization for Azure AD).
- Test the SSO login with a test user.
- Communicate the change to your team.
Updated 3 months ago
