Password settings
To improve the security of your customer data, enforce specific password settings that are applied to the platform's users when they log in with a username and password. These settings do not affect logins with Google or single sign-on.
For the accounts that have the identity domain enabled, there is an option to set up custom password settings.
You can change it in Settings > Project Settings > Security > Password settings.
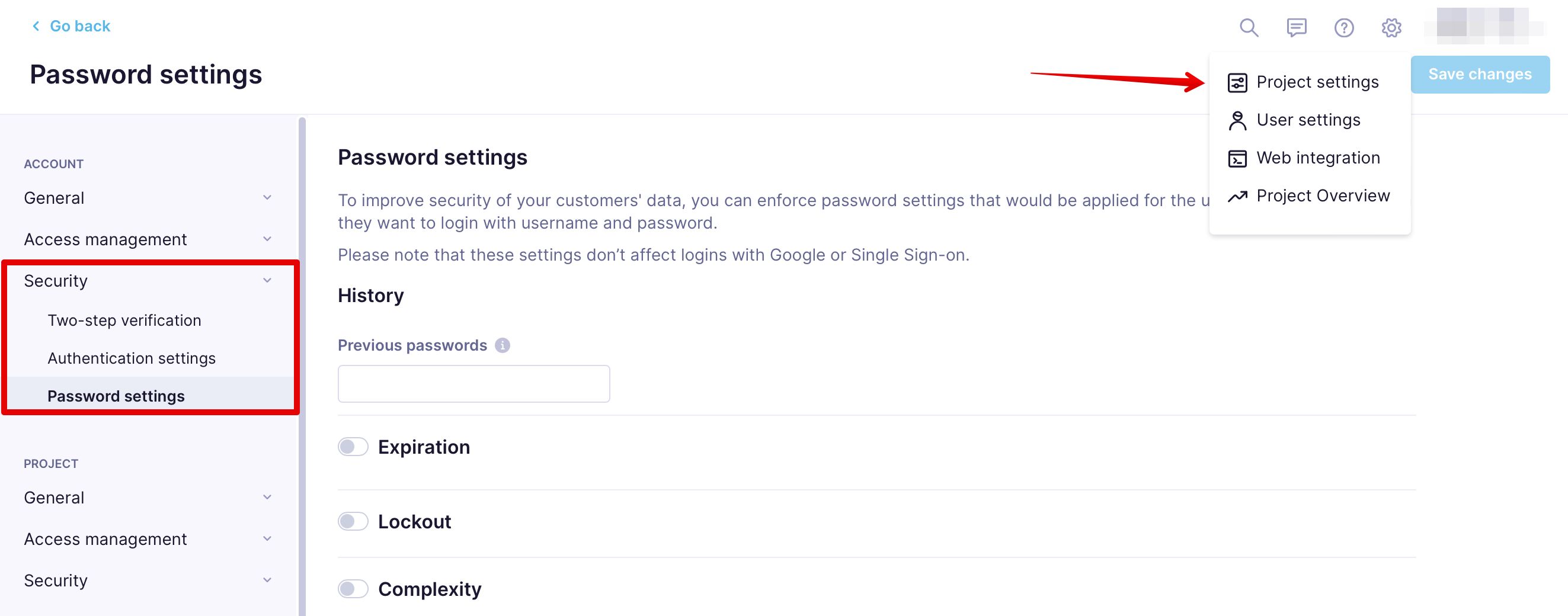
We encourage you to set up the following settings:
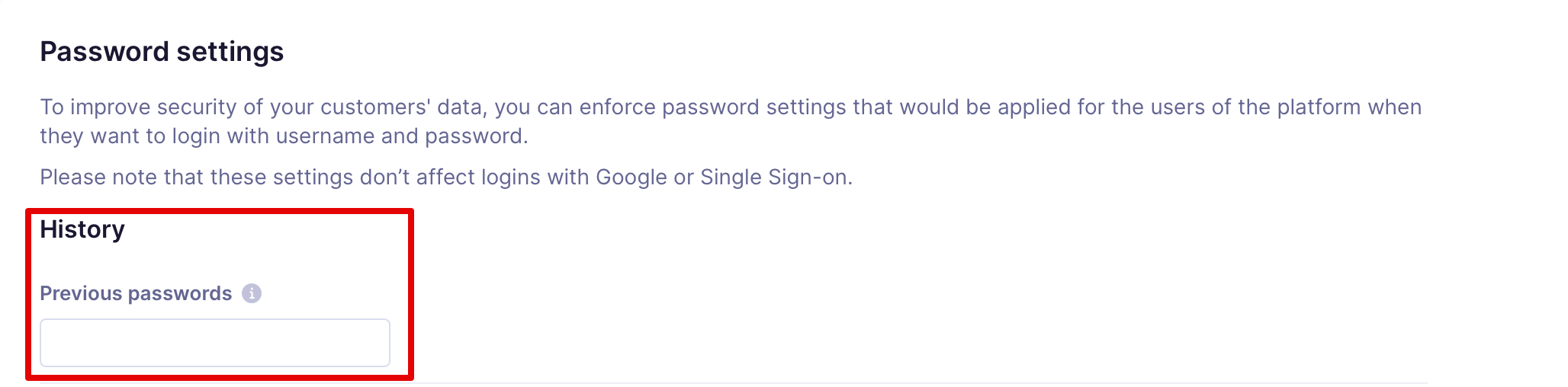
Password history
By filling in the Previous passwords, you indicate the number of passwords stored in history that cannot be reused.
Users cannot use a password that was already used. The default setting is that you cannot change the password to an existing one. If this setting is changed, the users wouldn't be able to use the selected number of passwords that they have used.
Warning
If you change the number of passwords stored in the history to a lower number, the previous ones will be deleted.
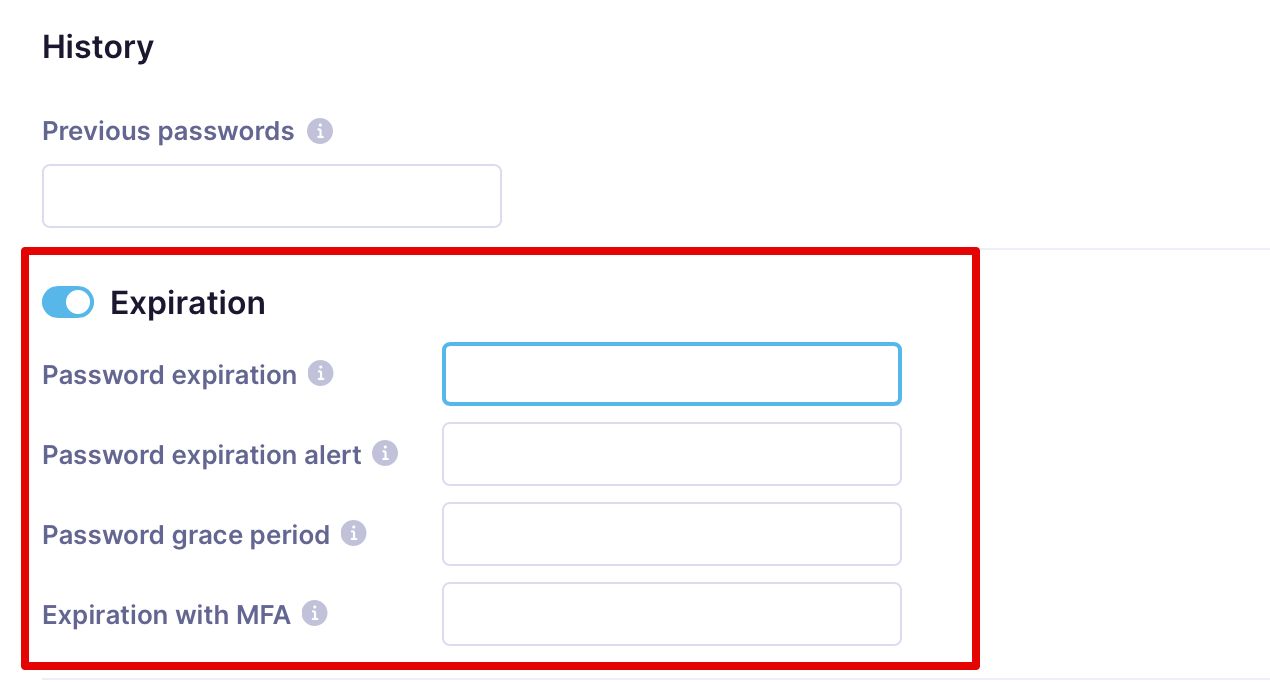
Password expiration
You can change default settings for multi-tenant instances or set up your own on the single-tenant instances.
- Password expiration: Indicates the number of days after which the user is forced to change their password.
- Password expiration alert: Indicates the number of days before the due password expiration to notify the user about this mandatory change.
- Password grace period: Indicates the number of days after a password expires when a user can change it.
- Expiration with MFA: Indicates the number of days after which a user with MFA enabled is forced to change their password.
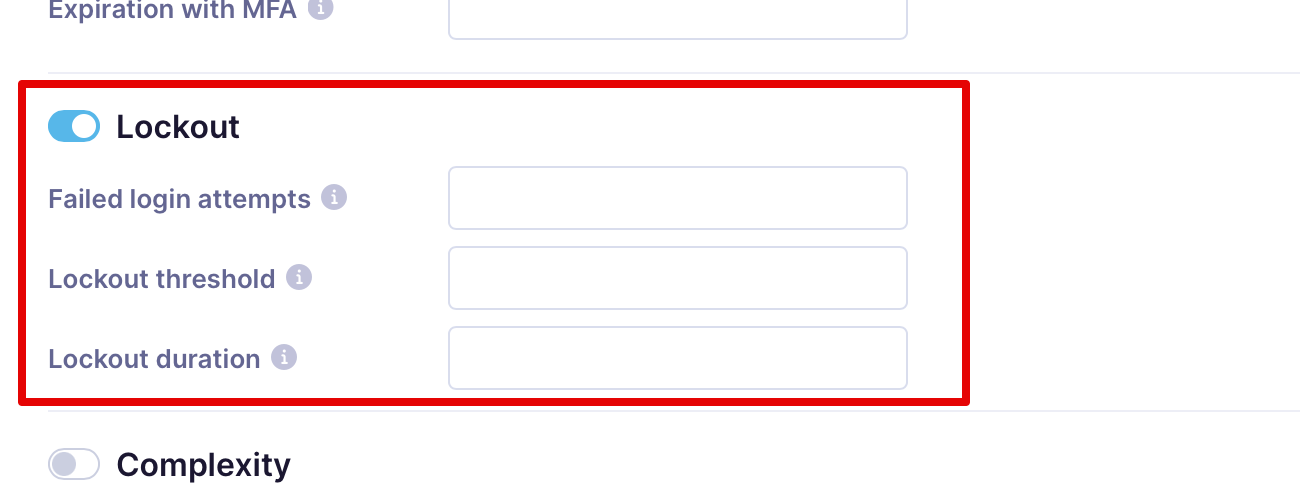
Lockout
This setting allows you to decide if the user is automatically locked after several unsuccessful attempts to log in.
- Failed login attempts:Indicates the number of failed login attempts after which the user account will be locked.
- Lockout threshold:Indicate the number of minutes from the first failed login until the failed login attempts counter resets.
- Lockout duration: Indicates the days that must pass until a user account is unlocked and can attempt to log in.
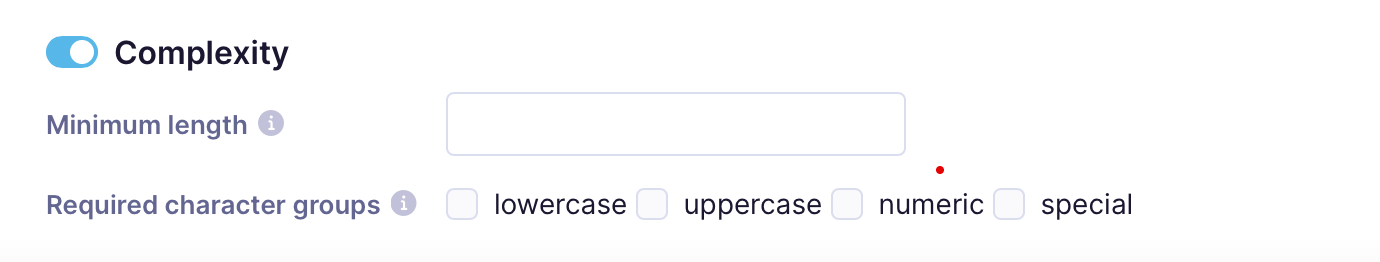
Password complexity
Here, you can change the default password complexity. However, if the instance (mainly multi-tenant instances) already has some instance-wide settings, these must be fulfilled. For example, on multi-tenant instances, the password must be at least 8 characters.
- Minimum length: Indicates the minimum number of characters a password must contain.
- Required character groups: Indicates the mandatory character groups a password must contain (lowercase, uppercase, numeric, and special).
Note
We recommend requiring at least 8 characters for password complexity.
Updated over 1 year ago
