Role-based access management
Unified login
For unified login setup, refer to the Unified login new and changed roles.
Bloomreach Engagement uses role-based access control to protect your data from unauthorized access. This system ensures that only the right people can access personal data or specific modules.
With Bloomreach Engagement, you can define and manage users with specific permissions, such as editing, viewing, or exporting customer data and running campaigns. You can also set different access levels for each user at the project or account level, tailored to their specific roles.
To do this, go to Settings > Project settings > Access management where you can select from, assign, and modify specific access rights.
Project limit
In each project, there is a limit of 1,000 users.
Role-based access control
Role-based access control (RBAC) groups small sets of specific permissions and accesses under "roles" that can be assigned to team members by the Admin. Admins can decrease the risk of major mistakes and security breaches by carefully restricting users' access to perform only the tasks they really need.
Invite a new project member
You can invite new users to your project and choose a role for them. They must accept your invitation, and until they do, they will show up under pending invitations.
For security reasons, the invitation is valid for 7 days. After that, the invited user cannot accept it, and the Administrator or Super Admin needs to resend the invitation.
While the invitation is pending, you can change the specific role and permissions. You can also adjust user access even after they accept the invitation. So, if you accidentally invite someone with the wrong role or permissions, don’t worry. The Project Administrator can change the role at any time.
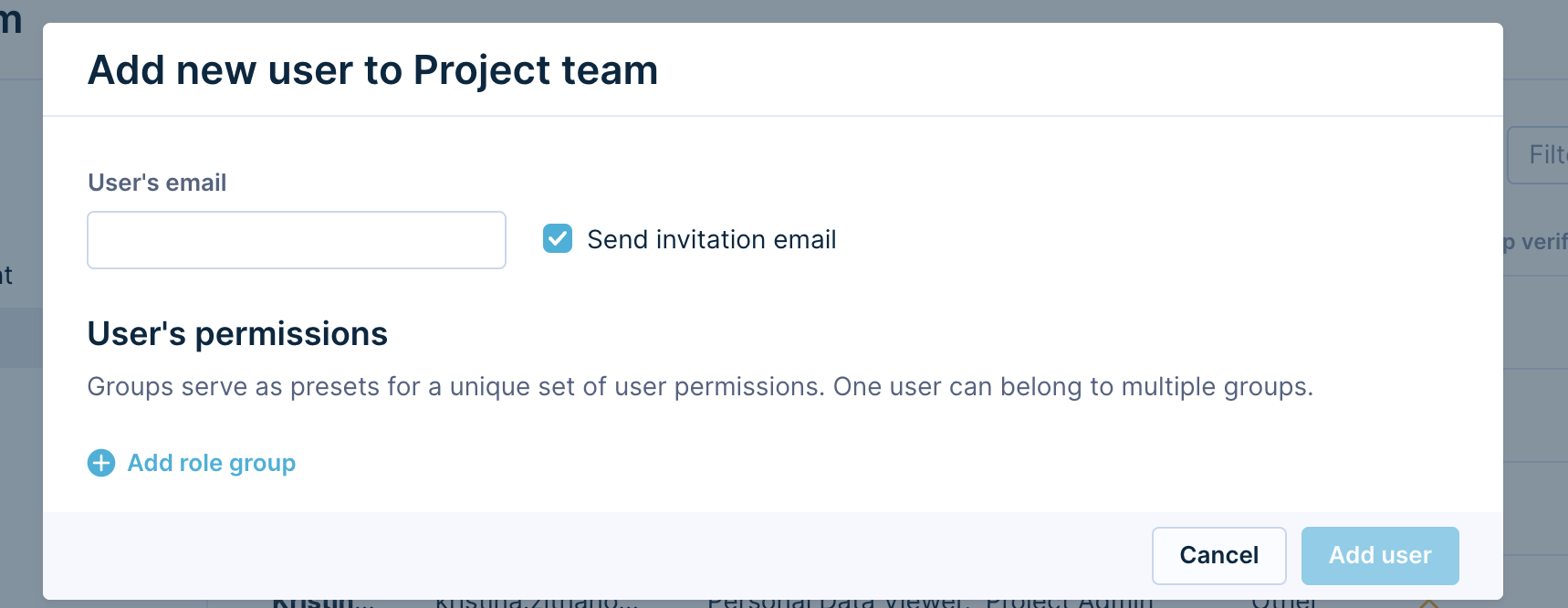
Configure permissions
To change a user’s project role in the project, hover over their name and click the Edit button on the right side in the Project team tab. You can choose multiple roles from a list. Bloomreach Engagement has several predefined roles, and you can also create your own custom roles to meet your needs.
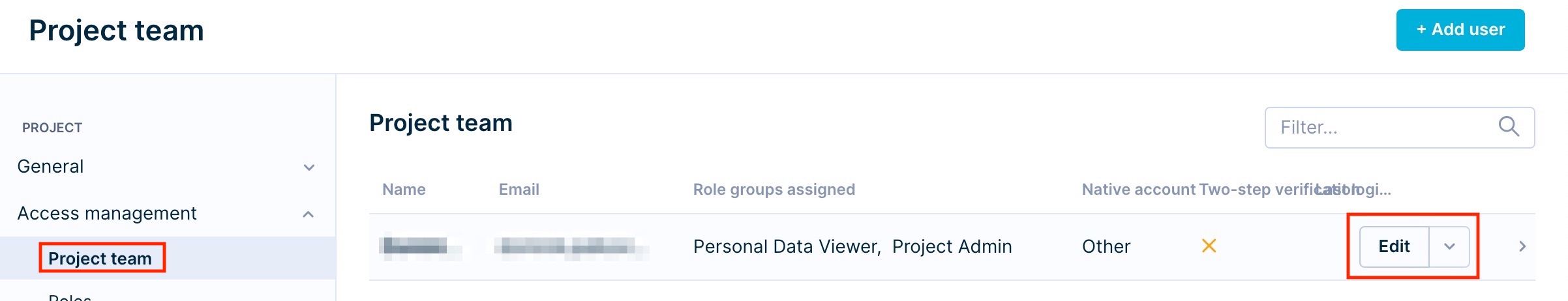
Assign multiple roles
You can assign multiple roles to each user by scrolling down their individual access permission setup and selecting Add role group. Then, in Project team you can see all individual roles and their descriptions under that person's name.
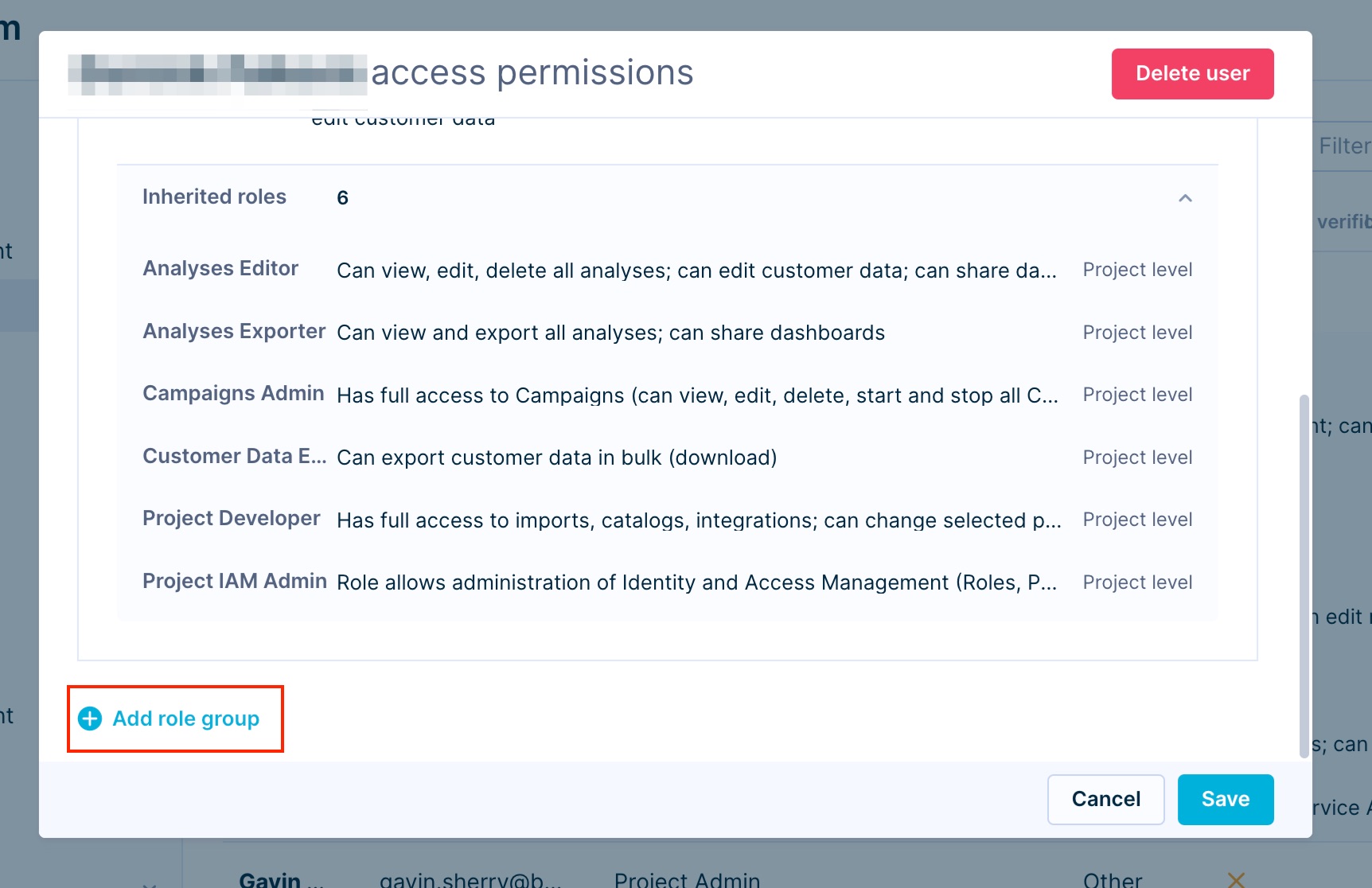
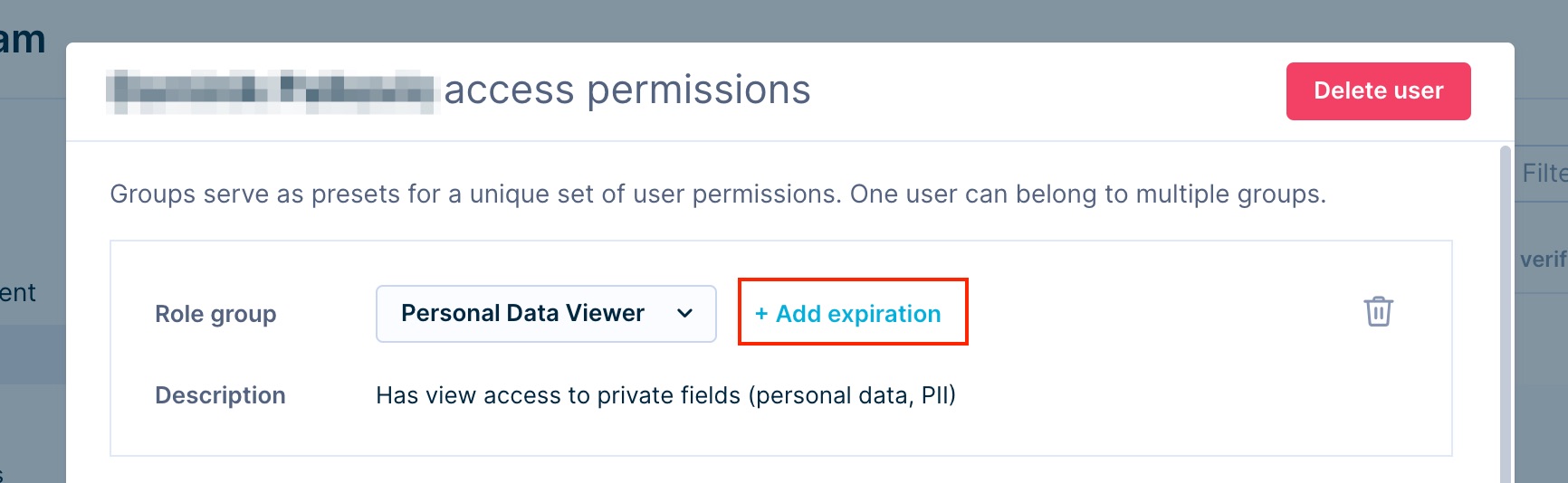
Temporary roles
The administrator can grant the user a temporary role by setting an expiration date in the user interface. Select the icon Add expiration and select the exact day and time that the user's role will expire. Expired roles are visible in the interface but are not active and do not grant any permissions. We recommend setting expiration for highly sensitive roles, such as Admin roles and Personal Data Viewer.
Permission hierarchy
Roles naming hierarchy
There are several out-of-the-box access roles in Bloomreach Engagement. To help you understand the scope of each role, they all follow the following naming convention: The first word or two represents the section of the application, and the later the extent of the permission.
Regarding the extent of the permission, there are levels of roles with an increasing set of permissions, creating a hierarchy of roles, as described in the flowchart below. Higher-level roles inherit all permissions from the lower ones, and lower levels never allow functions from higher-level roles. For example, while an Admin has access to all other functions, sole Editors cannot publish or export from Bloomreach Engagement (they can only do the task they are assigned and abilities hierarchically beneath them). All standalone roles follow this hierarchy and naming.
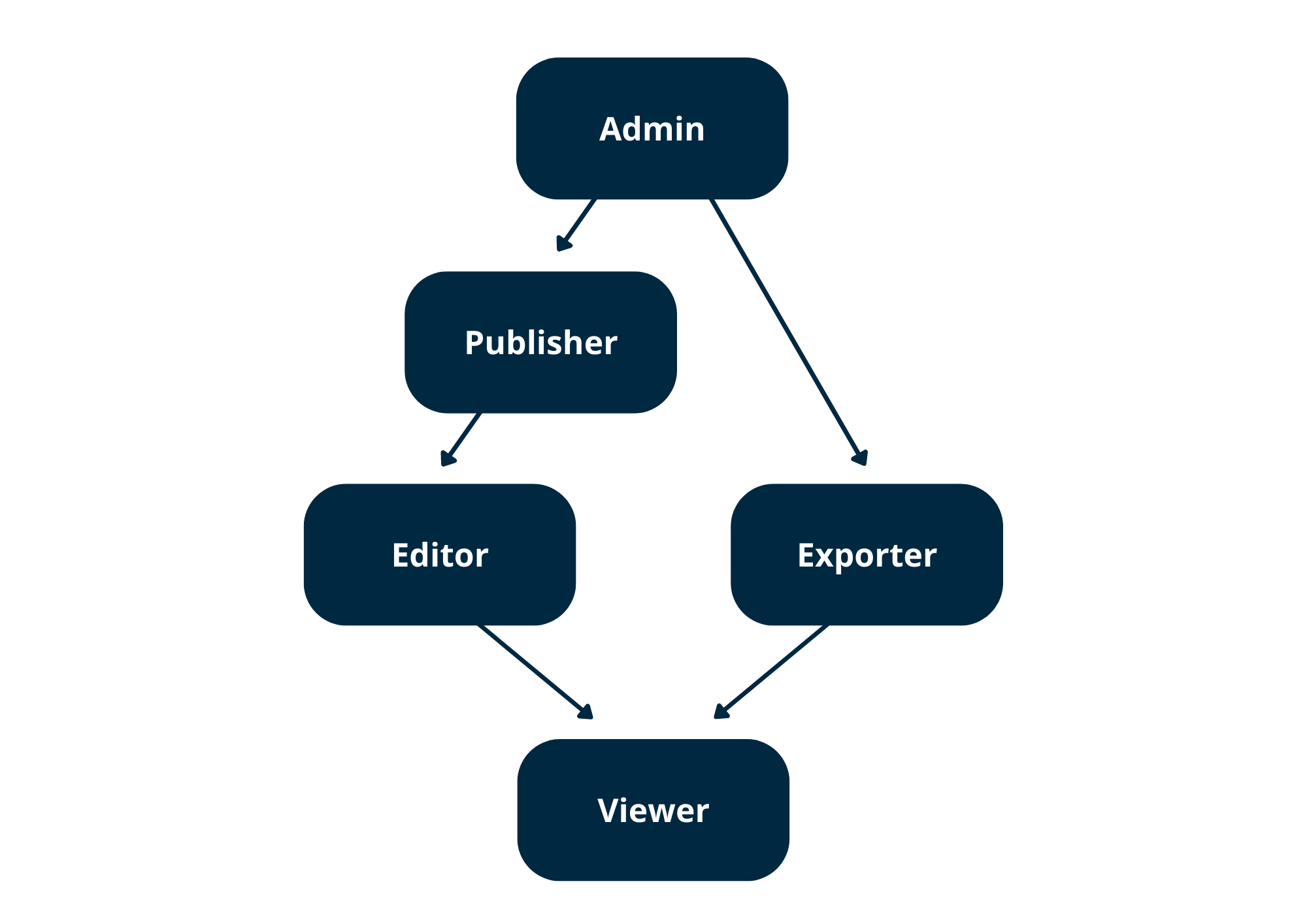
- Admin: Has full access to Campaigns (can view, edit, delete, start, and stop all campaigns; can edit running Campaigns; can change Campaigns settings) and can edit consent settings and customer data, excluding customer consents.
- Approver: Can only approve specific actions.
- Editor: Can write and delete access and modify and delete objects.
- Exporter: Can export or download data from the Bloomreach Engagement application.
- Publisher: Can execute access and trigger an action that may immediately impact the end customers or make objects publicly available.
- Requester: Can create a request.
- Viewer: This is read-only access. Viewer cannot modify objects.
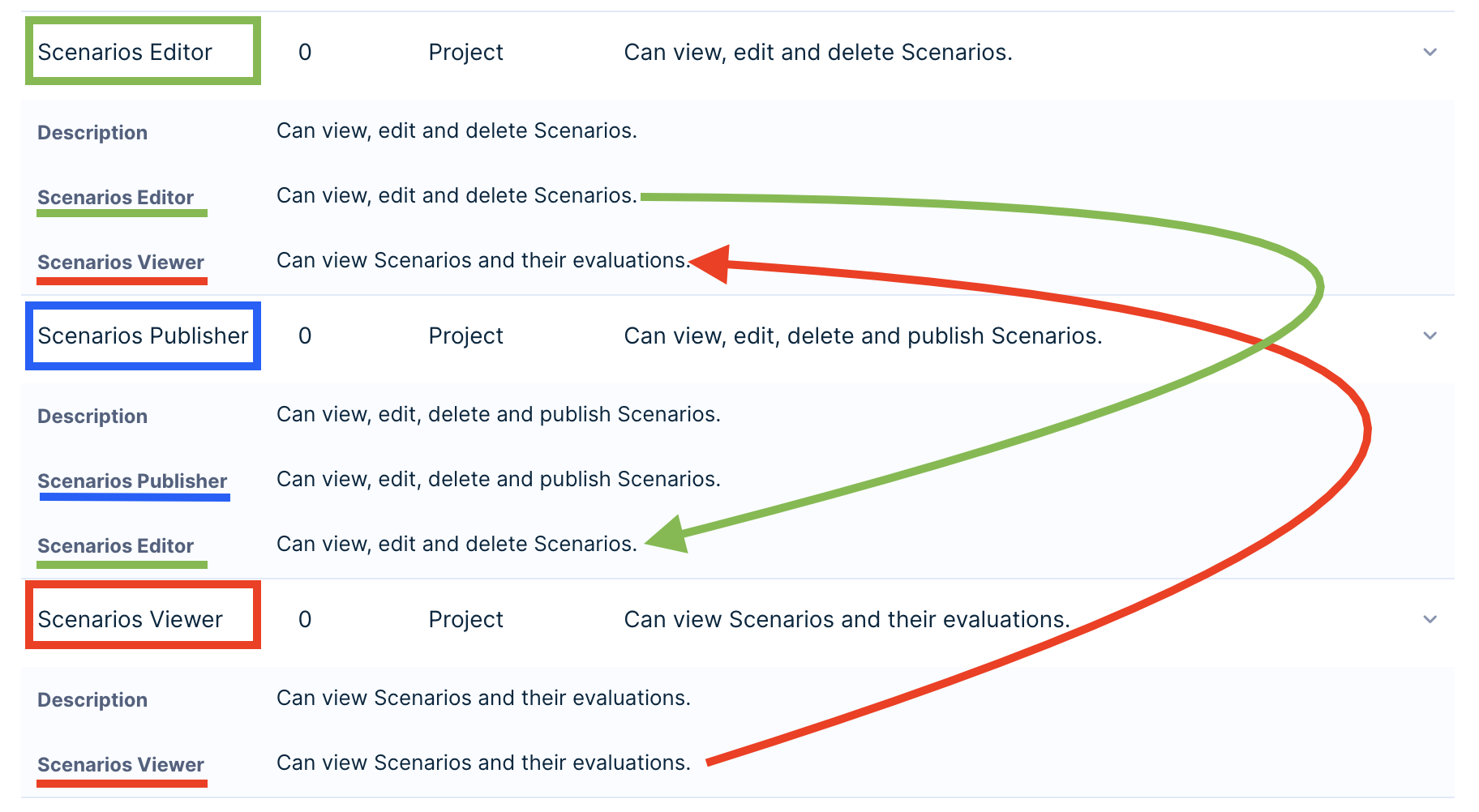
Permissions hierarchy example
The lowest-level role, the viewer, has its set of defined permissions.
The higher-level role, the editor, has their own set of permissions and those of the viewer.
And the publisher has their set of permissions and those of the editor, which also include those of the viewer.
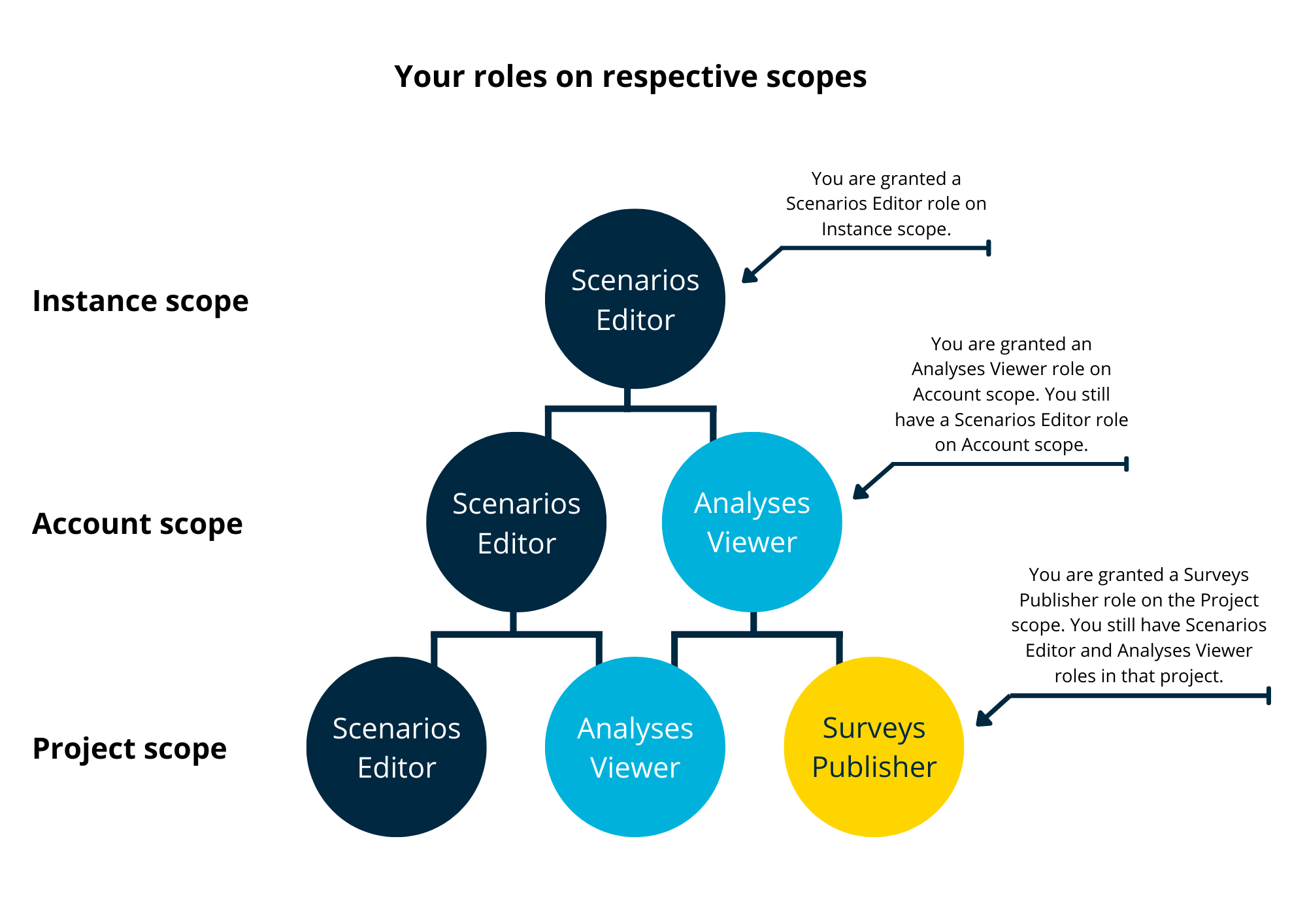
Permission scopes hierarchy
Be aware of the hierarchy between Instances, Accounts, and Projects. Roles granted on a higher scope (account) are applied to all lower scopes (project). If users operate on their own single-tenant instance, that instance has the highest hierarchy (instance > account > project).
For example, if a user is granted Analyses Viewer on the Account scope, the user will have the Analyses Viewer role in all projects under that account.
Roles assigned to users on an instance scope are applied to all accounts and projects within the instance. Roles assigned to users on account scope are applied to all projects within the account.
Ensure Project Safety by granting a role on the correct Scope
Roles assigned to users on an instance scope are applied to all accounts and projects within the instance. Roles assigned to users on account scope are applied to all projects within the account. This might be critical, as you might be granting Account rights to someone, who is supposed to see or edit one Project only.
Roles
Predefined roles
Several predefined standalone and non-standalone roles come out of the box. Those can be assigned to your project's members and users. All standalone roles follow the naming and hierarchy of roles described above.
In addition, there are several non-standalone roles set up by Bloomreach Engagement that allow access to specific actions.
Note
A user can have multiple roles assigned, but each user must have at least one standalone role to be able to access the project.
The following is the list of all predefined roles in Bloomreach Engagement.
| Role type | Description | Standalone |
|---|---|---|
| Account Admin | Has full access to accounts, projects, customer data within an account, account access management, and account-specific settings; can edit group access | Yes |
| Account IAM Admin | Manages account or project team, user invitations, user groups, and custom roles; manages all account security settings; manages account single sign-on (SSO) settings (excluding mapping roles) | Yes |
| Account Temporary Access Approver | Can approve temporary access requests on the Account and Project level | No |
| Account User (Legacy) | Can open account; can view account overview dashboards | Yes |
| Analyses Editor | Can view, edit, and delete all analyses (reports, segmentations, etc.); can edit customer data; can manage and share dashboards | Yes |
| Analyses Exporter | Can view and export all analyses; can share dashboards | Yes |
| Analyses Viewer | Can view all analyses | Yes |
| SSO Account Admin | Has full account access and can log in using the backup magic login link method | Yes |
| Campaigns Admin | Has full access to Campaigns (can view, edit, delete, start, and stop all Campaigns; can edit running Campaigns; can change Campaigns settings); can edit customer data - excluding customer consents; can edit consent settings | Yes |
| Campaigns Editor | Can view, edit, and delete Campaigns; can import data, edit customer data - excluding consents; can view, edit, and delete Catalogs. Can update, edit and save a file in the Asset Manager | Yes |
| Campaigns Viewer | Can view Campaigns and their evaluations | Yes |
| Customer Data Exporter | Can export customer data in bulk (download) | Yes |
| Email Campaigns Editor | Can view, edit and delete Email Campaigns; can view Catalogs, can create and edit Snippets | Yes |
| Email Campaigns Publisher | Can view, edit, delete, and publish Email Campaigns; can view Catalogs | Yes |
| Email Campaigns Viewer | Can view Email Campaigns and their evaluations; can view Catalogs | Yes |
| Experiments Editor | Can view, edit and delete Experiments | Yes |
| Experiments Publisher | Can view, edit, delete, and publish Experiments | Yes |
| Experiments Viewer | Can view Experiments and their evaluations | Yes |
| Exports Module Admin | Has full access to set up Exports of customer data, including PII | Yes |
| Personal Data Viewer (flag) | Has view access to private fields (PII) | No |
| Project Admin | Has full access to everything in projects and to project access management; can edit customer data, including consents; can create and start tags in the Tag Manager | Yes |
| Project IAM Admin | Manages project teams, user invitations, custom roles, and two-step verification | Yes |
| Project Developer | Has full access to imports, catalogs, integrations (including approval); can change selected project settings; can view customer data, can create and start tags in the Tag Manager | Yes |
| Project Temporary Access Approver | Can approve temporary access requests on the Account level | No |
| Project User (Legacy) | Can open projects and view customer data | Yes |
| Recommendation Editor | Can view Segmentations and view, edit, and delete Recommendations; can view Catalogs | Yes |
| Recommendation Viewer | Can view Recommendations and Segmentations; can view Catalogs | Yes |
| SMS Campaigns Editor | Can view, edit and delete SMS Campaigns; can view Catalogs | Yes |
| SMS Campaigns Publisher | Can view, edit, delete, and publish SMS Campaigns; can view Catalogs | Yes |
| SMS Campaigns Viewer | Can view SMS Campaigns and their evaluations; can view Catalogs | Yes |
| Technical Support | Has roles: Analyses Editor and Analyses Exporter, Campaigns Admin, and Customer Data Exporter. Can create and start tags in the Tag Manager | Yes |
| Temporary Access Approver | Can approve temporary access requests | No |
| Weblayers Editor | Can view, edit and delete Weblayers | Yes |
| Weblayers Publisher | Can view, edit, delete, and publish Weblayers | Yes |
| Weblayers Viewer | Can view Weblayers and their evaluations | Yes |
The special role of "Personal Data Viewer" grants access to private fields (personal data, PII). Bloomreach Engagement predefined roles never include this role. Personal Data Viewer must be granted explicitly or included in your custom roles.
To read more about the roles and see which specific roles are inherited, find the role in Access management > Roles.
Standalone role required
Each user must have at least one standalone role to access the project. If a user does not have any standalone role, for example, their role is Personal Data Viewer, they will have a problem logging into the project.
Granular roles
Bloomreach Engagement allows you to assign finely detailed roles to your project members, not limiting you to choose from broader predefined roles listed above. Remember, a user can have multiple roles assigned, but each user must have at least one standalone role to be able to access the project.
| Role | Description | Standalone |
|---|---|---|
| Account Usage Viewer | Can view the Usage Dashboard on the Project and the Account level | Yes |
| Customers Viewer | Can view Customer attributes and events; can view Catalogs | Yes |
| Customers Consent Editor | Can grant and revoke customer Consents; can view Customer attributes and events | Yes |
| Customers Editor | Can view, edit, and delete Customer attributes and events; can view Catalogs | Yes |
| Dashboard Editor | Can view, edit, delete, and share dashboards. | Yes |
| Data Manager Viewer | Can view Data Manager | Yes |
| Data Manager Definition Editor | Can view, edit, and delete Data manager definitions | Yes |
| Event Analyses Editor | Can view, edit, and delete Event Analyses (for example, Funnels, Trends, Retentions, Flows, and Geo Analyses) | Yes |
| Event Analyses Exporter | Can view, edit, delete, and export Event Analyses (for example, Funnels, Trends, Retentions, Flows, and Geo Analyses) | Yes |
| Event Analyses Viewer | Can view Event Analyses (for example, Funnels, Trends, Retentions, Flows, and Geo Analyses) and their results | Yes |
| Imports Admin | Can view, edit, and delete Imports and Catalogs | Yes |
| In-App-Message Editor | Can view, edit, and delete In-App-Message | Yes |
| In-App-Message Publisher | Can view, edit, delete, and publish In-App-Message | Yes |
| In-App-Message Viewer | Can view In-App-Message and their evaluations | Yes |
| Initiatives Editor | Can view, edit, and delete Initiatives | Yes |
| Integrations Editor | Can view, edit, and delete Integrations; can create already approved integration types (accepted Terms & Conditions) | Yes |
| Managed Endpoints Editor | Can view and edit Managed Endpoints; can view Catalogs | Yes |
| Managed Endpoints Publisher | Can view, edit, and publish Managed Endpoints; can view Catalogs | Yes |
| Managed Endpoints Viewer | Can view Managed Endpoints and their evaluations; can view Catalogs | Yes |
| Project Usage Viewer | Can view the Usage Dashboard on the Project level | Yes |
| Reports Editor | Can view, edit, and delete Reports | Yes |
| Reports Exporter | Can view, edit, delete, and export Reports | Yes |
| Reports Viewer | Can view Reports and their results | Yes |
| Scenarios Editor | Can view, edit, and delete Scenarios; can view Catalogs | Yes |
| Scenarios Publisher | Can view, edit, delete, and publish Scenarios; can view Catalogs | Yes |
| Scenarios Viewer | Can view Scenarios and their evaluations; can view Catalogs | Yes |
| Segmentations Editor | Can view, edit, and delete Segmentations | Yes |
| Segmentations Exporter | Can view, edit, delete, and export Segmentations | Yes |
| Segmentations Viewer | Can view Segmentations | Yes |
| Surveys Editor | Can view, edit, and delete Surveys | Yes |
| Surveys Publisher | Can view, edit, delete, and publish Surveys | Yes |
| Surveys Viewer | Can view Surveys and their evaluations | Yes |
Custom role
While Bloomreach Engagement predefines roles, you can set up your own custom roles. This allows you to add and combine several inherited roles to create a single role that would suit your specific needs. In other words, custom roles are stacked from predefined roles and inherit all their permissions and scope level.
- Go into the Project settings > Access Management > Roles.
- Click + Create custom role in the top right corner.
- Select + Add inherited role.
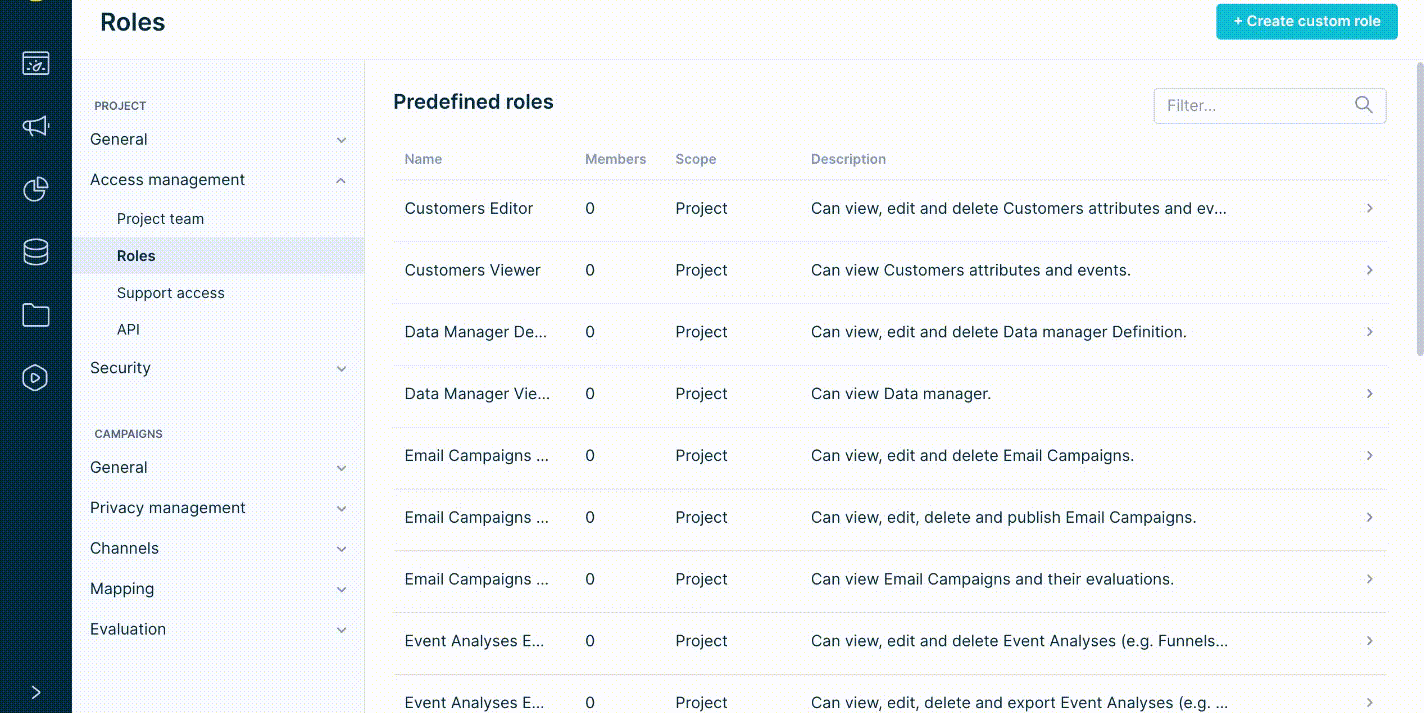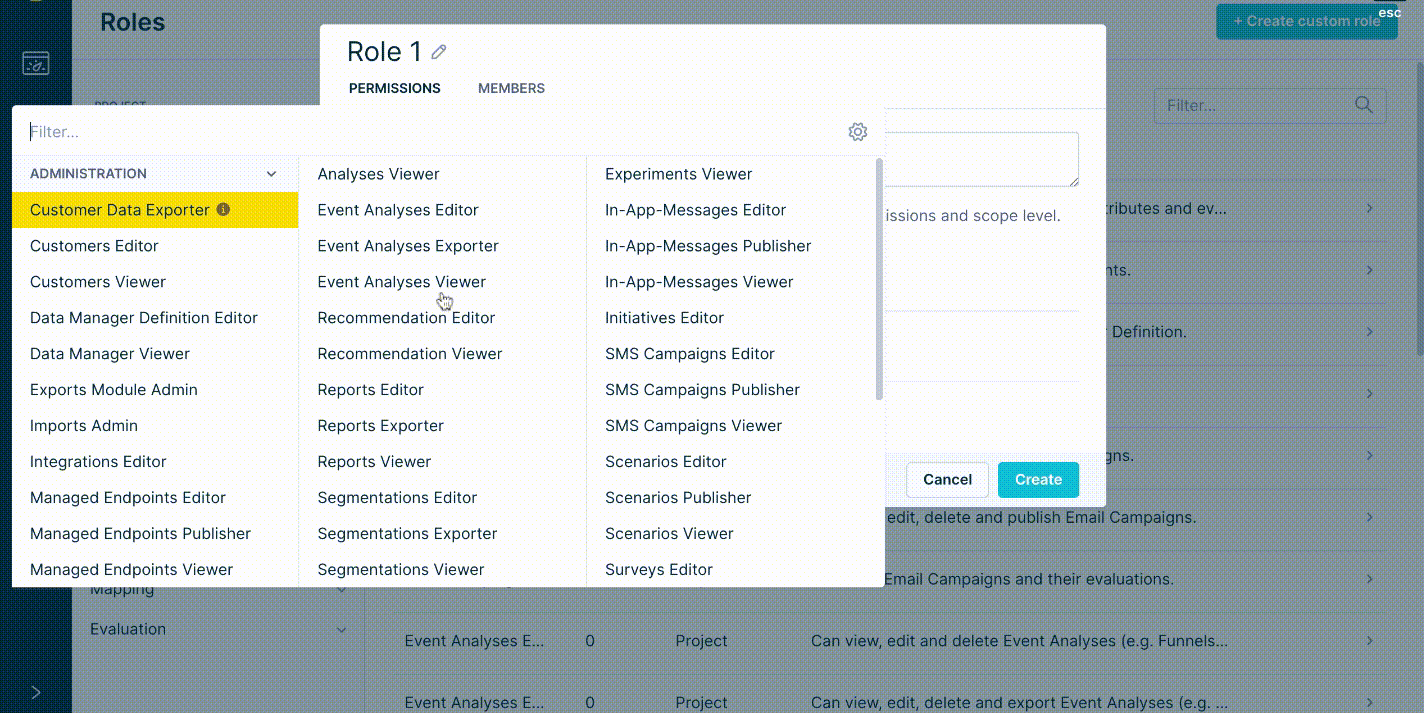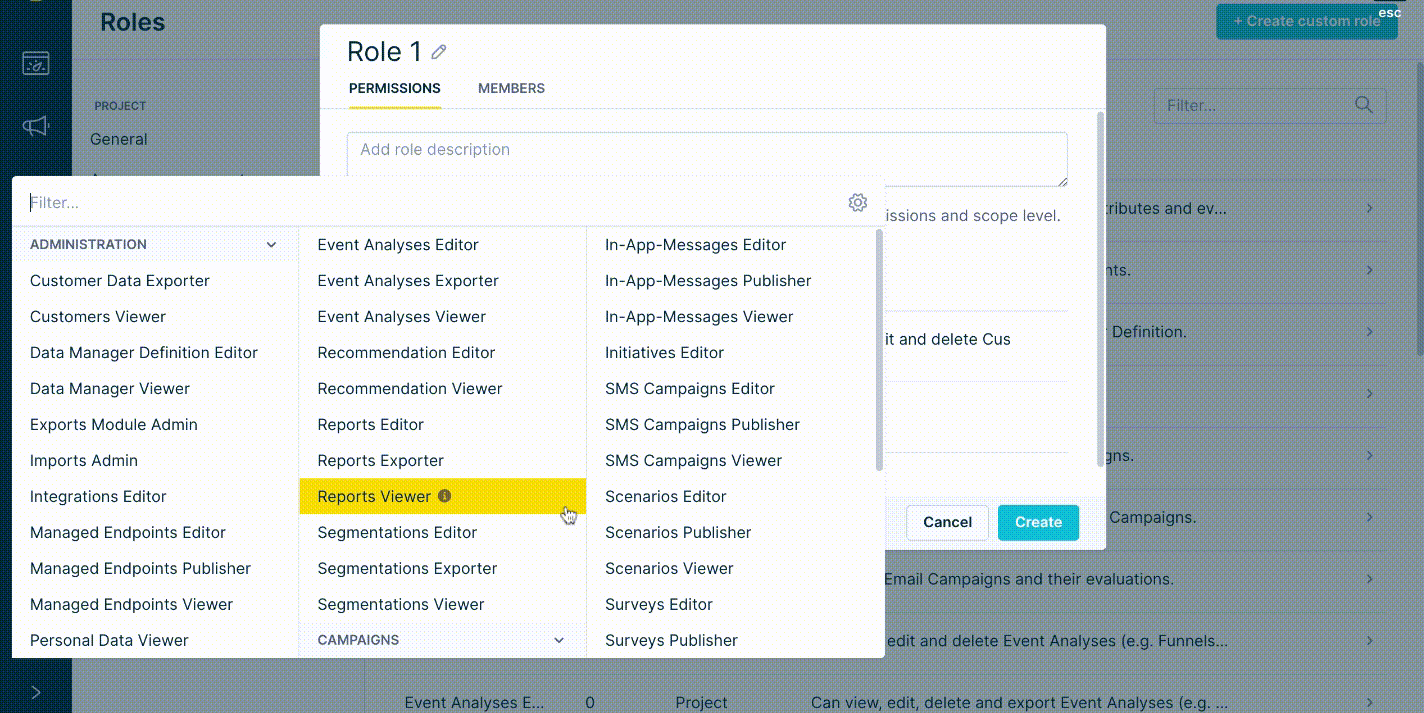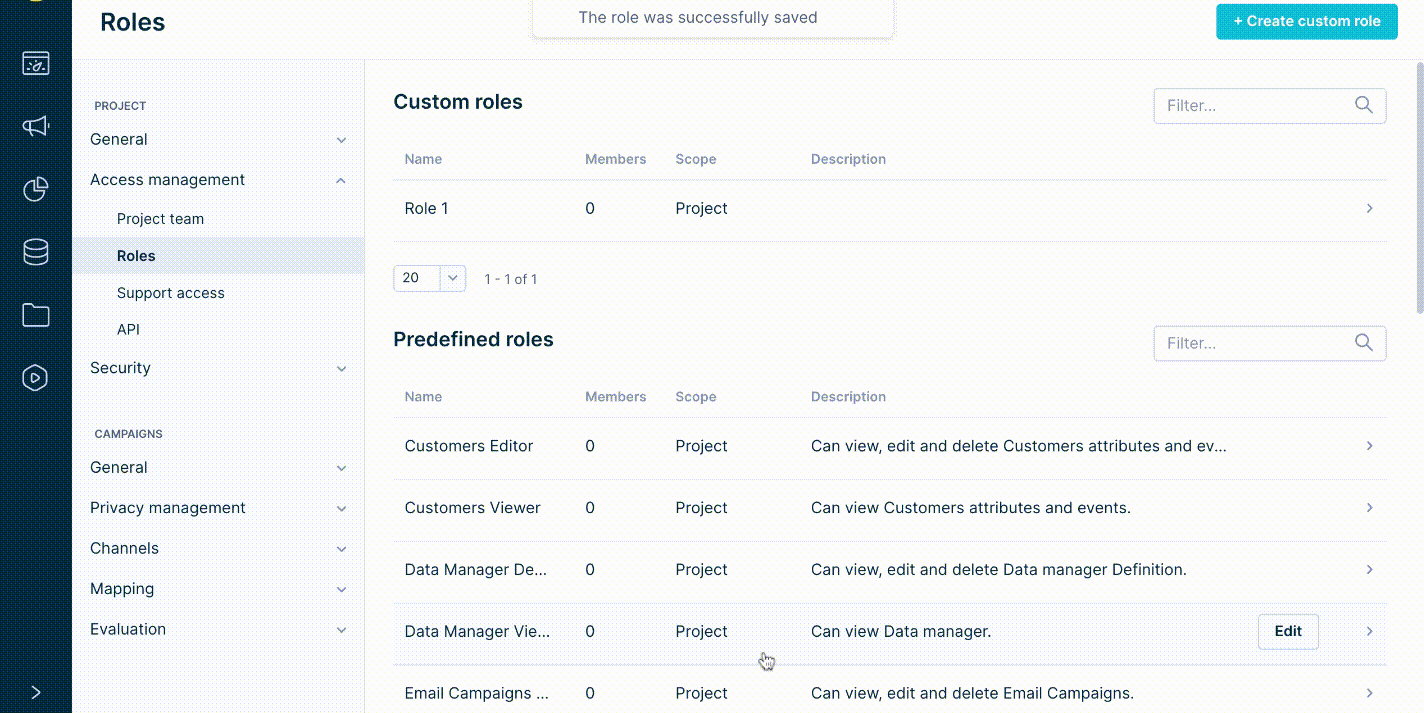
When there is a team with the same responsibilities and permissions operating the Bloomreach Engagement application, we do recommend creating a custom role. This custom role would inherit all required roles - allowing you to then only assign this single role to all team members. Furthermore, this makes it easier to see who is currently a member of this role on the Custom role Members tab.
Limitations
- Custom roles (user-defined) can be combined from multiple roles, but a permission cannot be removed from a particular role.
- There can be a maximum of 100 custom roles.
- One custom role can include a maximum of 32 roles.
Assign users to access groups
If you want to add more security and refine further what exactly specific users with their roles can edit within Bloomreach Engagement, you can assign users to access groups. Learn more about User Groups Management in our documentation.
Important
Removing a user only removes their access. However, all analyses and campaigns they created will remain.
Identity domain
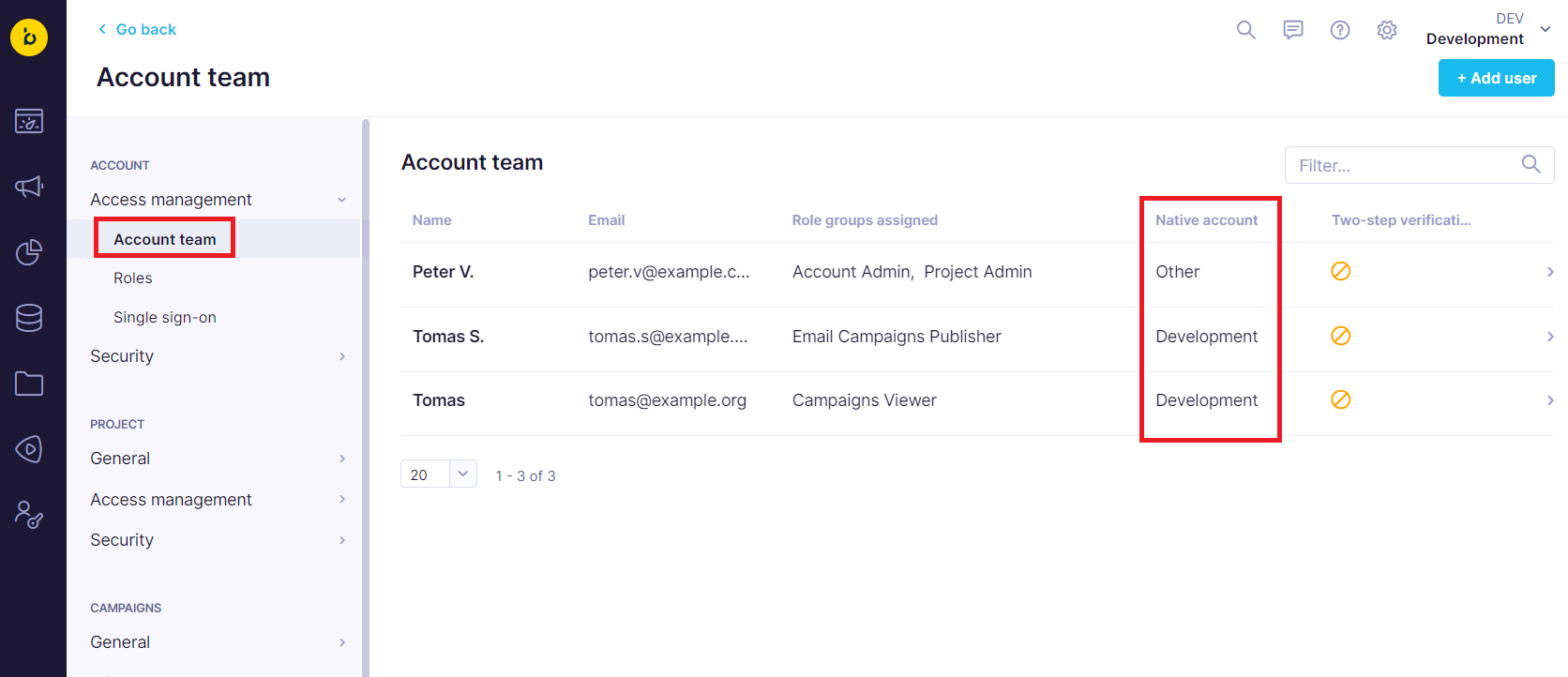
Under Access Management > Account team/Project team, you can check who is part of your identity domain.
The identity domain serves to solve the tension between users having only one user account but access to multiple accounts and projects. It is unclear what policies to follow when enforcing some requirements (such as requiring an email and password or SSO to log in). During the login process, it is unclear what accounts would be accessed since users have access to multiple, and these have different settings.
However, the identity domain solves this issue. When users are invited to the instance for the first time, an account is set up where they were invited as their native domain. Following this, the policies and settings from this account would apply to the user.
The identity domain supports the following settings:
- Single Sign-on
- Authentication methods
- Password settings
Check who is in your identity domain under Access Management > Account team/Project team.
There is a column called Native account. If the name matches the account name, the user belongs to this account, and the settings apply. If there is "Other", the user is from a different account. We do not reveal the native account of the users to other clients to avoid revealing what other accounts are on the instance.
If you need to change the native account for your user, please get in touch with our support team.
Invite external users
When you want to simplify access for your internal users choosing SSO, you face a challenge with the need for agency users to access the application. Since the external users aren't included in the company's identity provider (for example, Azure or Okta), SSO prevents these users from accessing the application.
To solve this, Bloomreach Engagement has introduced an option to invite users as external users. This enables the activation of Single Sign-on for all internal users while still allowing external contractors access to log in.
SSO admin access
You need an SSO Account admin role to have the option of adding external users available.
Add a new external user
- Go to Settings > Account team/Project team > Access Management > + Add User.
- Enable External user toggle.
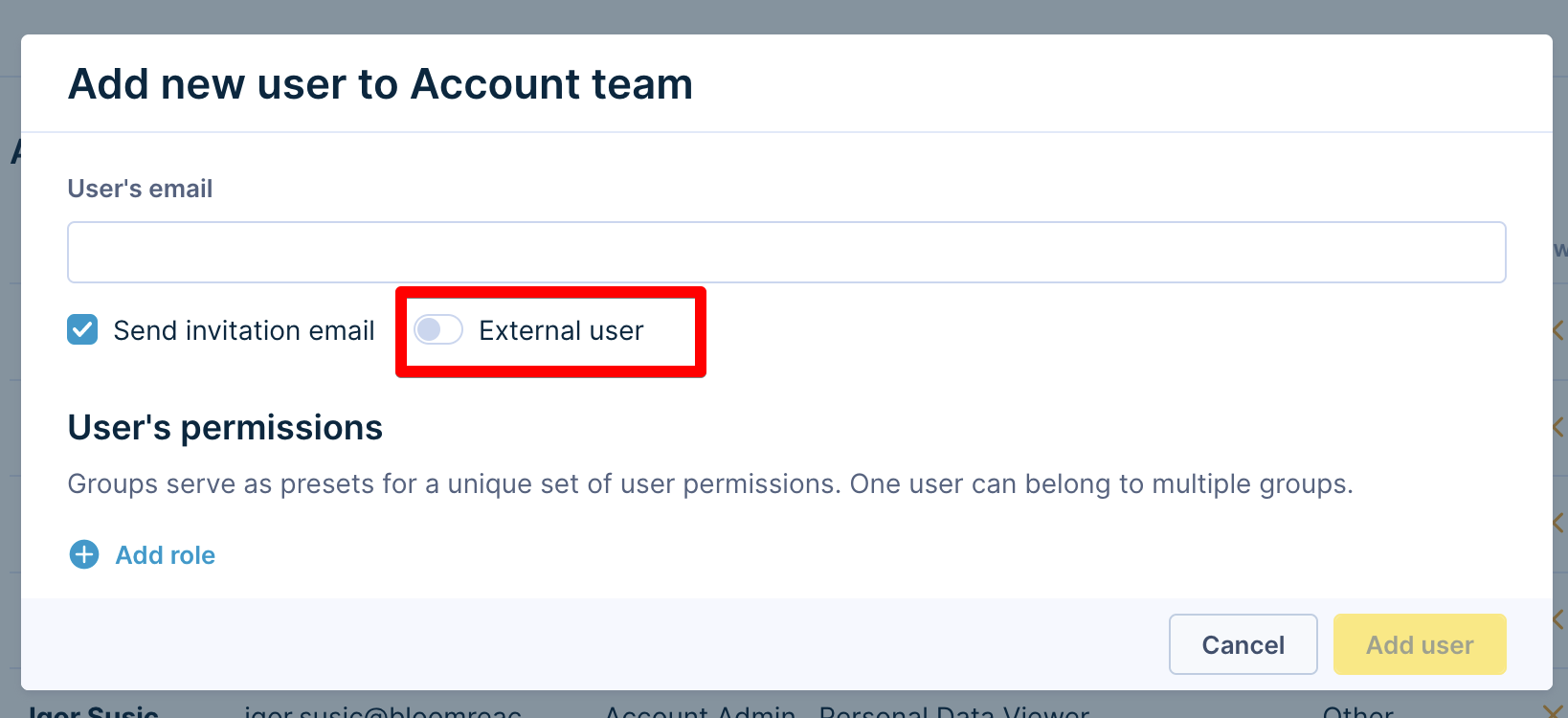
Activating this setting will trigger a warning to inform you that the pre-set account password policy does not apply to external users.
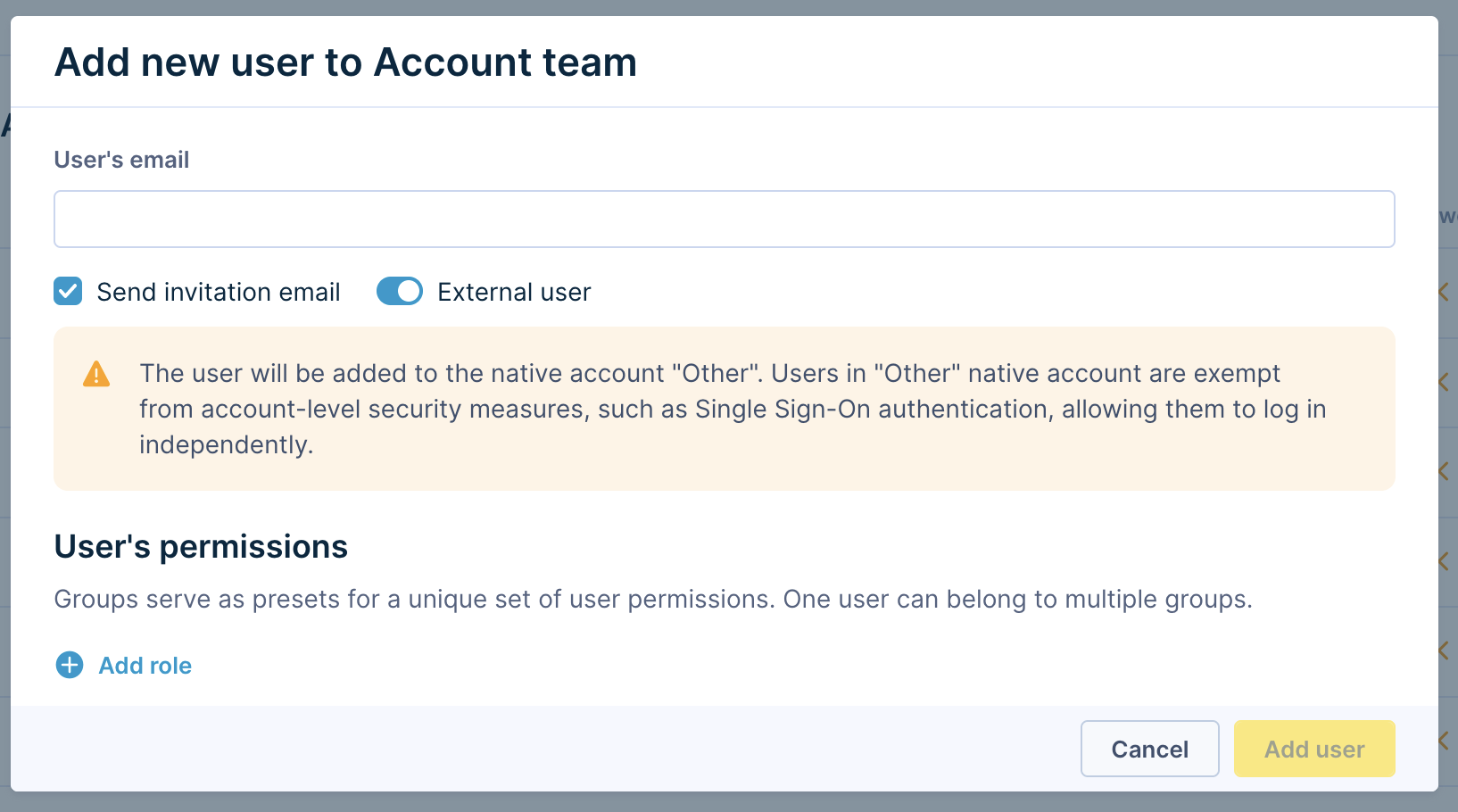
Important
Adding a user as external cannot be undone. To switch external user to internal user afterwards, contact customer support.
SSO disabled
External users can log in with their email and password or via Google login only. SSO login method is not available to them.
Change user to external user
If you have a user who won’t be able to use a selected login method (for example, SSO), you can remove them from your native account and mark them as an external user.
Go to Settings > Account team/Project team > Access Management, choose the user, click Edit > Mark as external user.
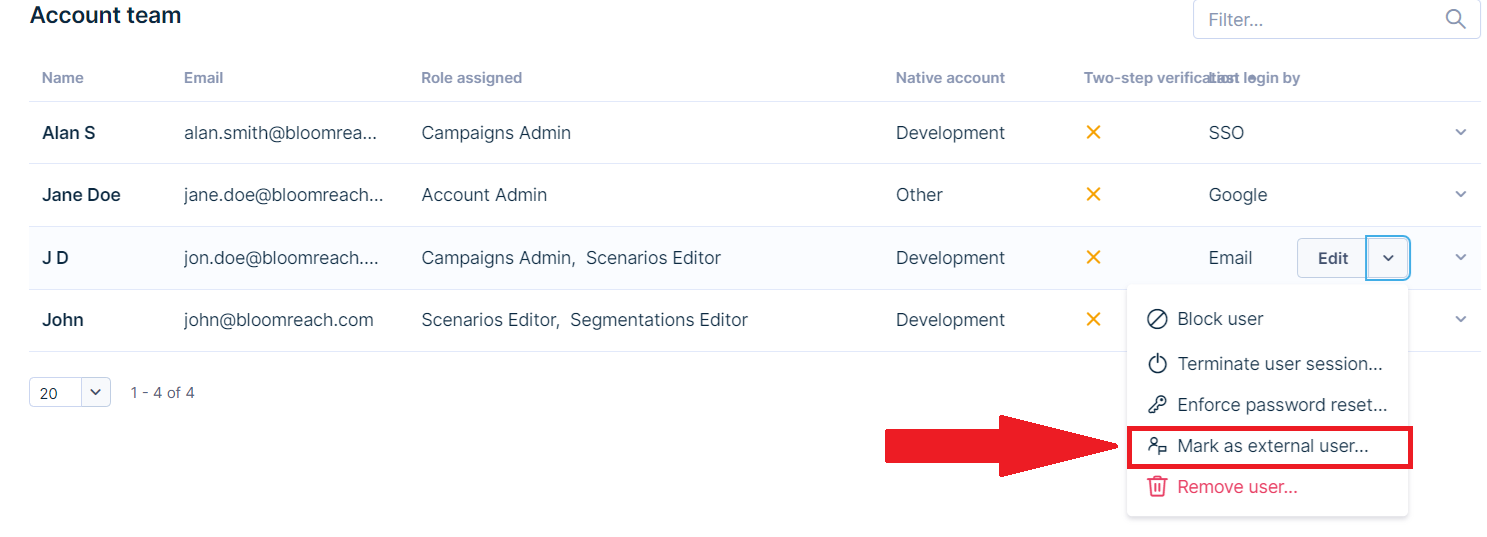
Once you mark a user as external, you cannot revert this operation. To switch an external user to an internal user afterward, contact Customer Support.
Error "Forbidden 403"
When user roles are changed, there is a slight delay before the new permissions are applied. Be aware that permission changes are not applied immediately – it may take up to one minute to propagate changes into all components. If you still get the error after waiting a few minutes and reloading the application and think you should have access or permissions for this action, contact our Support.
Updated 3 months ago
