Unified SSO authorization for Azure Active Directory
Data hub rollout
Engagement customers are being upgraded to unified login in several phases. Your registered support contacts will be notified when the login experience is upgraded for your organization. If your account hasn't been upgraded yet, the pre-existing Administration documentation still applies.
Single sign-on (SSO) authorization is an extension of SSO authentication. It enables you to define user privileges and control what they can access within Bloomreach products.
This guide explains how to configure SSO authorization for Azure Active Directory (Azure AD).
Note
The SSO authorization uses
role_mappingto determine user permissions. For role mapping configuration details, see the Unified SSO overview guide.
Prerequisites
Before configuring SSO authorization for Azure AD, you must complete the SSO authentication setup in Azure AD. You’ll also need:
- Admin role in Bloomreach.
- Admin access to your Azure AD account.
- Understanding of your organization's role structure.
- Active SSO feature enabled on your account.
Configure role mapping in Azure AD
Add the role mapping claim in Azure AD
Azure AD sends the role_mapping value as a SAML attribute. This value must match the mapping role names you configure in Bloomreach.
- Go to your Azure AD dashboard.
- Go to Manage > Enterprise Applications.
- Select your Bloomreach SSO application.
- From the Manage menu, select Single sign-on.
- Click Edit in the Attributes & Claims section.
- Click + Add new claim.
- Configure the new claim:
- Name:
role_mapping. - Source: Attribute.
- Source attribute: Select your preferred value (for example,
user.department).
- Name:
- Click Save.
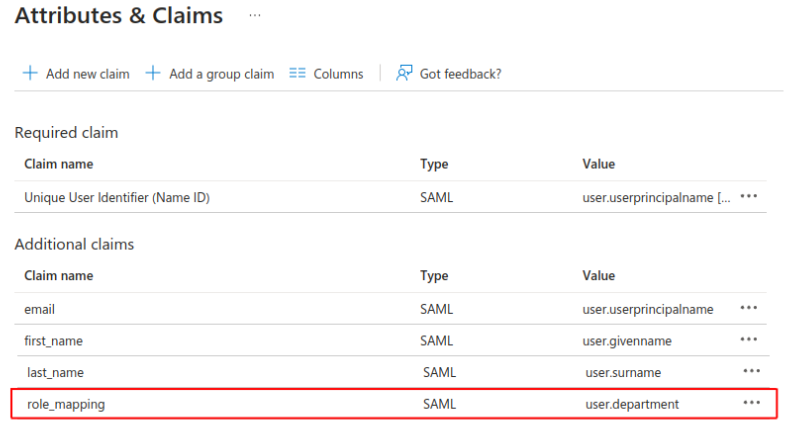
Role mapping claims in Azure AD.
Sarah's department in Azure AD is "Product Management." When you configure role_mapping to use user.department, Azure AD sends "Product Management" during login. You'll map this value to permissions in Bloomreach next.
Using group membership for role mapping
You can use Azure AD group membership instead of user attributes. This allows sending multiple groups as part of the claim, giving you flexibility to assign different roles based on group combinations.
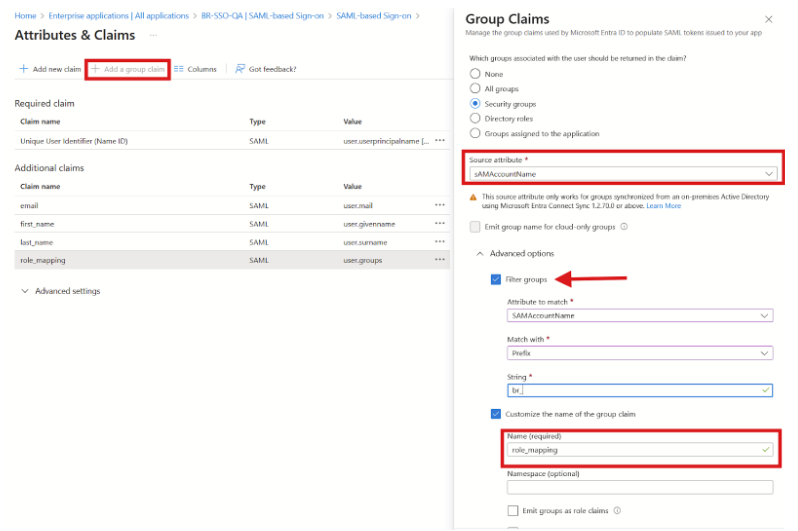
Group role mapping claims in Azure AD.
Set up authorization in Bloomreach
Configure role mapping in Bloomreach to connect identity provider values with application permissions.
Create role mapping
- Go to Administration > Users > Mapping roles.
- Click New mapping role.
- Enter a mapping role name that exactly matches the
role_mappingvalue from your identity provider to the “Incoming role name” field. - Add an optional description for the mapping role.
- In the Permissions section, select an application (for example, Engagement).
- Choose at least one scope (the part this role can access in Bloomreach):
- Workspace: Users can access all projects within a workspace (for example, department-wide access).
- Project: User can access only specific projects you select (for example, project-specific members or limited access).
- Select one or more roles for the chosen scope.
- Click Add permission to add roles for additional scopes or applications.
- Click Save to finish role mapping setup.
Important
The role mapping must include all scopes and roles that users with this mapping will need.
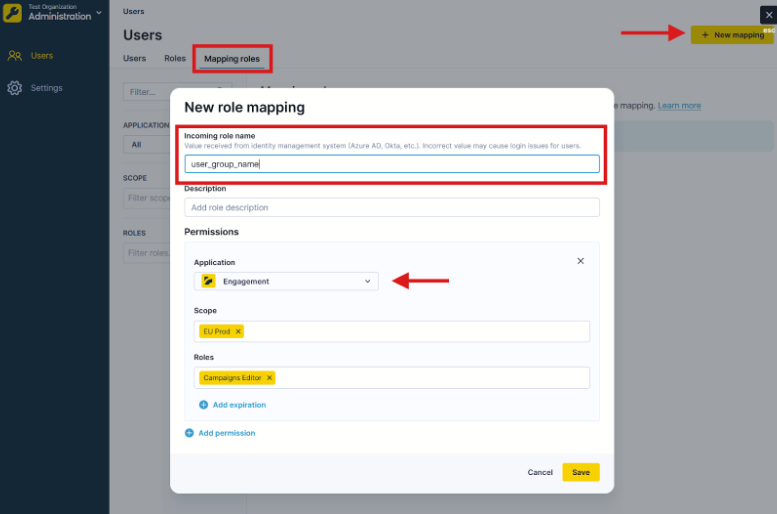
Create role mapping in Bloomreach.
Sarah's Azure AD sends "Product Management" as her role_mapping value. In Bloomreach, you create a mapping role with "Product Management" as the incoming role name and assign it Campaign Editor access in Engagement. When Sarah logs in, she automatically receives these permissions.
Enable SSO authorization
After creating and configuring the role mapping setup, activate SSO authorization in Bloomreach.
Important prerequisites
- Ensure you have created a role mapping setup containing SSO admin role to prevent locking out of configuration.
- Verify that mapping roles in Bloomreach match
role_mappingclaim values in Azure AD. Incorrect configuration can prevent login acces.
- Go to Administration > Settings > Single sign-on > Preferences.
- Scroll to the bottom of the page.
- Enable Single sign-on authorization.
- Click Save changes.
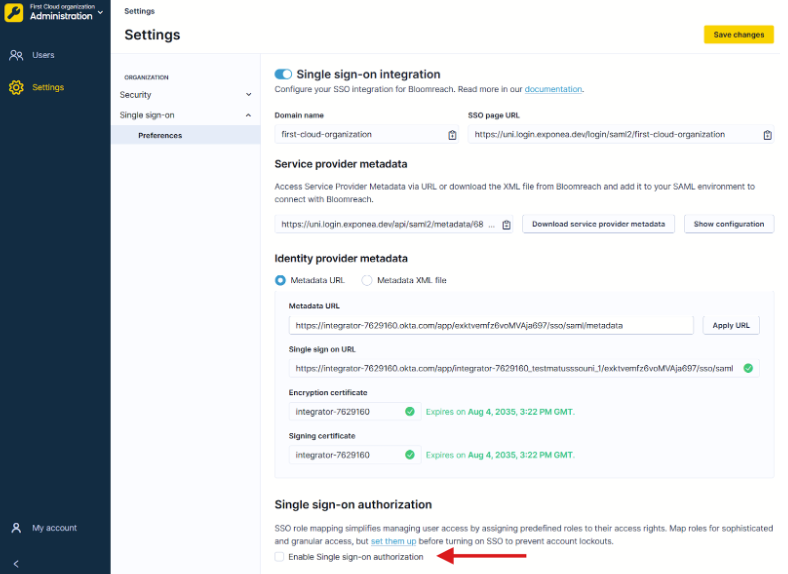
Enable SSO authorization in Bloomreach.
Users with the SSO Account Admin role can disable this option later if needed.
Next steps
- Invite your users to use the SSO login
- Manage user access and user roles
Updated 2 months ago
